Kathleen M. Carley, Director of the center for Computational Analysis of Social and Organizational Systems, ISR, Carnegie Mellon University, Pittsburgh, PA 15213, Office: 412-268-6016, FAX: 412-268-2338; Email: kathleen.carley@cs.cmu.edu
Problem: Terrorist organizations have network structures that are distinct from those in typical hierarchical organizations - they are cellular and distributed. While most commanders, politicians and intelligence agents have at least an intuitive understanding of hierarchies and how to affect their behavior, they have less of an understanding of how to even go about reasoning about dynamic networked organizations. It is even more difficult to understand how such networks will evolve, change, adapt and how they can be destabilized. The DyNet project addresses this need.
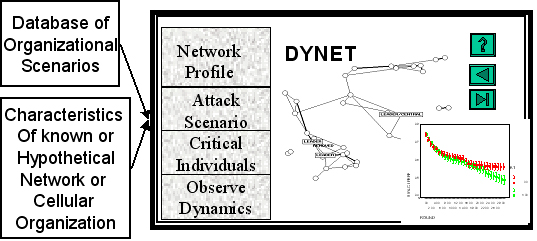
DYNET: A desktop tool for reasoning about dynamic networked and cellular organizations.
The purpose of the DyNet project is to develop the equivalent of a flight simulator for reasoning about dynamic networked organizations. Through a unique blending of computer science, social networks and organization theory we are creating a new class of tools for managing organizational dynamics. The core tool is DyNet - a reasoning support tool for reasoning under varying levels of uncertainty about dynamic networked and cellular organizations, their vulnerabilities, and their ability to reconstitute themselves. Using DyNet the analyst would be able to see how the networked organization was likely to evolve if left alone, how its performance could be affected by various information warfare and isolation strategies, and how robust those strategies were in the face of varying levels of information assurance.
DyNet is intended to be a desktop system that can be placed in the hands of intelligence personnel, researchers, or military strategists. Through hands-on what if analysis the analysts will be able to reason in a what -if fashion about how to build stable adaptive networks with high performance and how to destabilize networks. There are many applications for such a tool including: threat assessment; assessing information security risks in corporations; intel training; simulation of the red team in a gaming situation, and estimation of efficacy of destabilization policies. Currently an alpha version exists as a batch program (no visualization)and has been used to evaluate simple isolation strategies. The system can handle data on real networks.
Hungarian Translation courtesy of Elana Pavlet
Turkish Translation courtesy of Zoltan Solak
French Translation courtesy of Laura Beoschat
Urdu translation courtesy of ClothingRIC
Kazakh translation courtesy of Alana Kerimova
Greek translation courtesy of Nikolaos Zinas
Danish translation courtesy of Mille Erikson
Indonesian Translation courtesy of Jordan Silaen
Swedish Translation courtesy of Weronika Pawlak
Macedonian Translation courtesy of Jimmy Anastasovski
Portuguese Translation courtesy of Diana Gomes and Travel-Ticker.com
Russian Translation courtesy of Sandi Wolfe
Ukranian Translation courtesy of Sandi Wolfe
Slovenian Translation courtesy of Jurij Rodionov
Greek Translation courtesy of Hum2D